Hello, in this particular article you will provide several interesting pictures of phishing attacks and strategies to mitigate them. We found many exciting and extraordinary phishing attacks and strategies to mitigate them pictures that can be tips, input and information intended for you. In addition to be able to the phishing attacks and strategies to mitigate them main picture, we also collect some other related images. Find typically the latest and best phishing attacks and strategies to mitigate them images here that many of us get selected from plenty of other images.
 The Major Types of Phishing Attacks & How to Identify Them: The We all hope you can get actually looking for concerning phishing attacks and strategies to mitigate them here. There is usually a large selection involving interesting image ideas that will can provide information in order to you. You can get the pictures here regarding free and save these people to be used because reference material or employed as collection images with regard to personal use. Our imaginative team provides large dimensions images with high image resolution or HD.
The Major Types of Phishing Attacks & How to Identify Them: The We all hope you can get actually looking for concerning phishing attacks and strategies to mitigate them here. There is usually a large selection involving interesting image ideas that will can provide information in order to you. You can get the pictures here regarding free and save these people to be used because reference material or employed as collection images with regard to personal use. Our imaginative team provides large dimensions images with high image resolution or HD.
 Phishing Attacks And Strategies To Mitigate Them V2 Tools Provided By phishing attacks and strategies to mitigate them - To discover the image more plainly in this article, you are able to click on the preferred image to look at the photo in its original sizing or in full. A person can also see the phishing attacks and strategies to mitigate them image gallery that we all get prepared to locate the image you are interested in.
Phishing Attacks And Strategies To Mitigate Them V2 Tools Provided By phishing attacks and strategies to mitigate them - To discover the image more plainly in this article, you are able to click on the preferred image to look at the photo in its original sizing or in full. A person can also see the phishing attacks and strategies to mitigate them image gallery that we all get prepared to locate the image you are interested in.
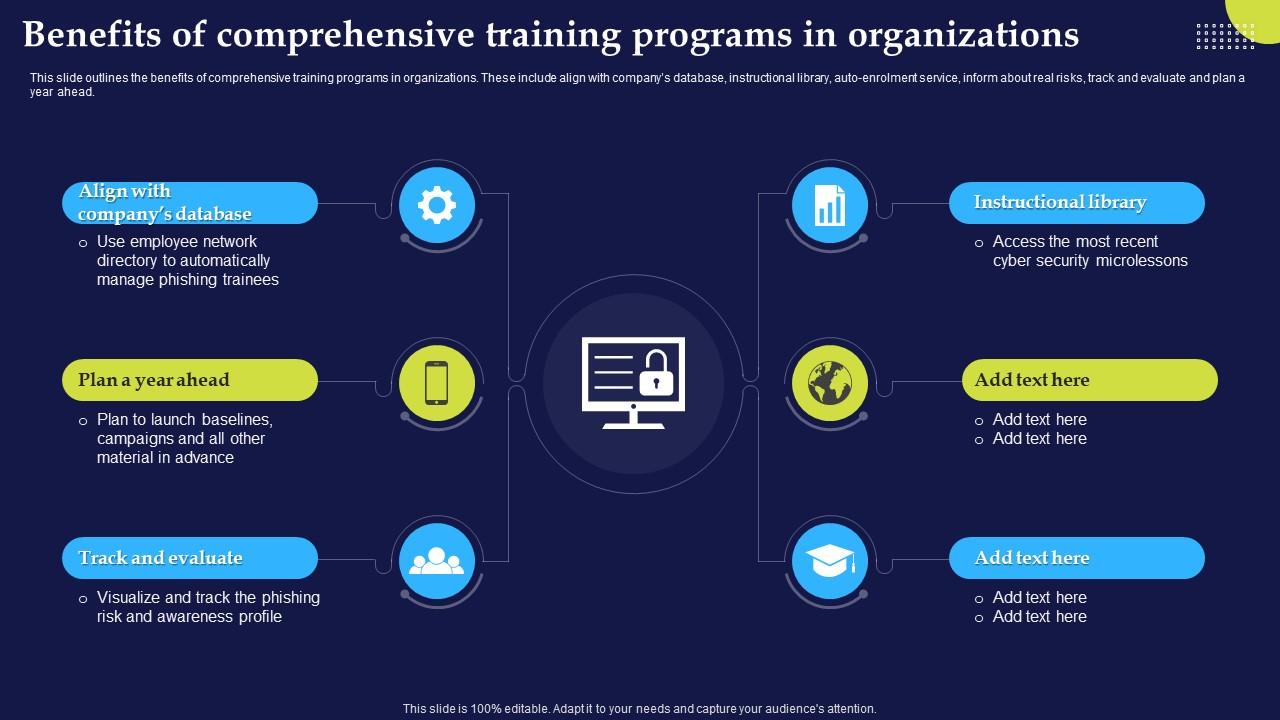 Phishing Attacks And Strategies To Mitigate Them V2 Benefits Of We all provide many pictures associated with phishing attacks and strategies to mitigate them because our site is targeted on articles or articles relevant to phishing attacks and strategies to mitigate them. Please check out our latest article upon the side if a person don't get the phishing attacks and strategies to mitigate them picture you are looking regarding. There are various keywords related in order to and relevant to phishing attacks and strategies to mitigate them below that you can surf our main page or even homepage.
Phishing Attacks And Strategies To Mitigate Them V2 Benefits Of We all provide many pictures associated with phishing attacks and strategies to mitigate them because our site is targeted on articles or articles relevant to phishing attacks and strategies to mitigate them. Please check out our latest article upon the side if a person don't get the phishing attacks and strategies to mitigate them picture you are looking regarding. There are various keywords related in order to and relevant to phishing attacks and strategies to mitigate them below that you can surf our main page or even homepage.
 K107 Working Process Of Cyber Phishing Attacks Phishing Attacks And Hopefully you discover the image you happen to be looking for and all of us hope you want the phishing attacks and strategies to mitigate them images which can be here, therefore that maybe they may be a great inspiration or ideas throughout the future.
K107 Working Process Of Cyber Phishing Attacks Phishing Attacks And Hopefully you discover the image you happen to be looking for and all of us hope you want the phishing attacks and strategies to mitigate them images which can be here, therefore that maybe they may be a great inspiration or ideas throughout the future.
 Phishing Attacks And Strategies To Mitigate Them V2 Measures For All phishing attacks and strategies to mitigate them images that we provide in this article are usually sourced from the net, so if you get images with copyright concerns, please send your record on the contact webpage. Likewise with problematic or perhaps damaged image links or perhaps images that don't seem, then you could report this also. We certainly have provided a type for you to fill in.
Phishing Attacks And Strategies To Mitigate Them V2 Measures For All phishing attacks and strategies to mitigate them images that we provide in this article are usually sourced from the net, so if you get images with copyright concerns, please send your record on the contact webpage. Likewise with problematic or perhaps damaged image links or perhaps images that don't seem, then you could report this also. We certainly have provided a type for you to fill in.
 Phishing Attacks And Strategies To Mitigate Them V2 About Vishing The pictures related to be able to phishing attacks and strategies to mitigate them in the following paragraphs, hopefully they will can be useful and will increase your knowledge. Appreciate you for making the effort to be able to visit our website and even read our articles. Cya ~.
Phishing Attacks And Strategies To Mitigate Them V2 About Vishing The pictures related to be able to phishing attacks and strategies to mitigate them in the following paragraphs, hopefully they will can be useful and will increase your knowledge. Appreciate you for making the effort to be able to visit our website and even read our articles. Cya ~.
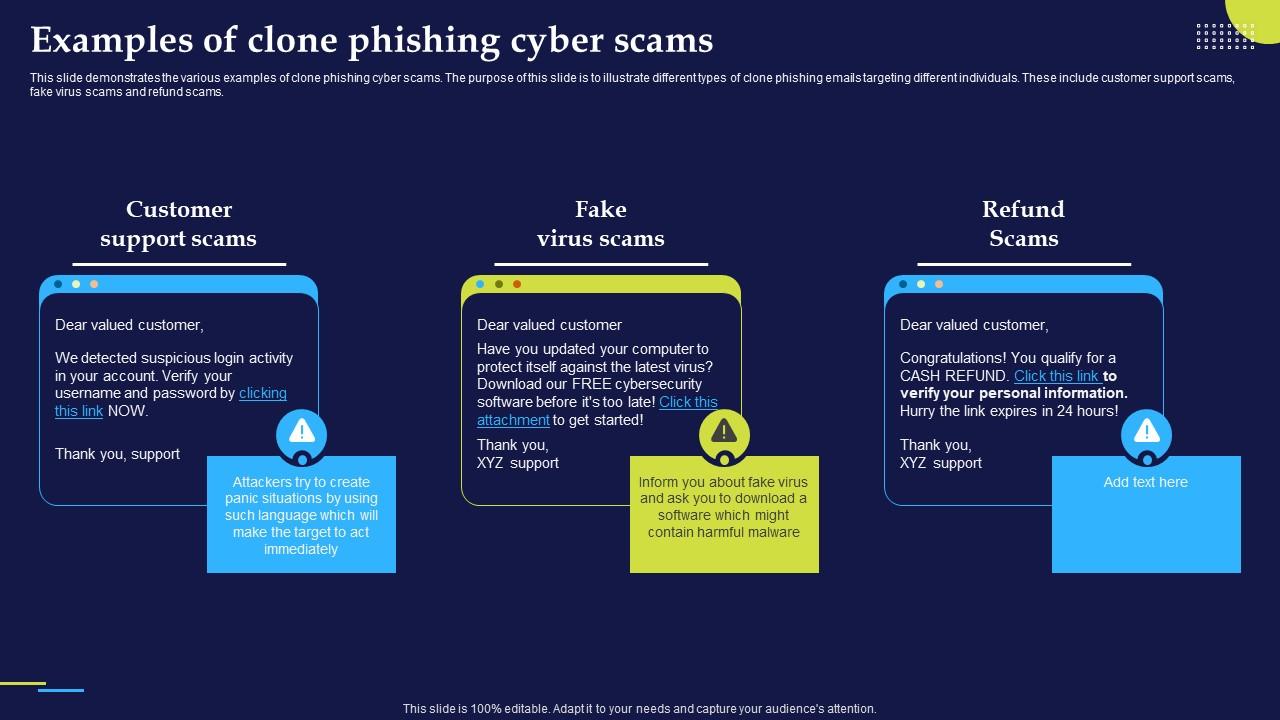 Phishing Attacks And Strategies To Mitigate Them V2 Examples Of Clone Phishing Attacks And Strategies To Mitigate Them V2 Examples Of Clone
Phishing Attacks And Strategies To Mitigate Them V2 Examples Of Clone Phishing Attacks And Strategies To Mitigate Them V2 Examples Of Clone
![]() Icons Slide For Phishing Attacks And Strategies To Mitigate Them PPT Icons Slide For Phishing Attacks And Strategies To Mitigate Them PPT
Icons Slide For Phishing Attacks And Strategies To Mitigate Them PPT Icons Slide For Phishing Attacks And Strategies To Mitigate Them PPT
 Phishing Attacks And Strategies To Mitigate Them V2 Checklist To Secure Phishing Attacks And Strategies To Mitigate Them V2 Checklist To Secure
Phishing Attacks And Strategies To Mitigate Them V2 Checklist To Secure Phishing Attacks And Strategies To Mitigate Them V2 Checklist To Secure
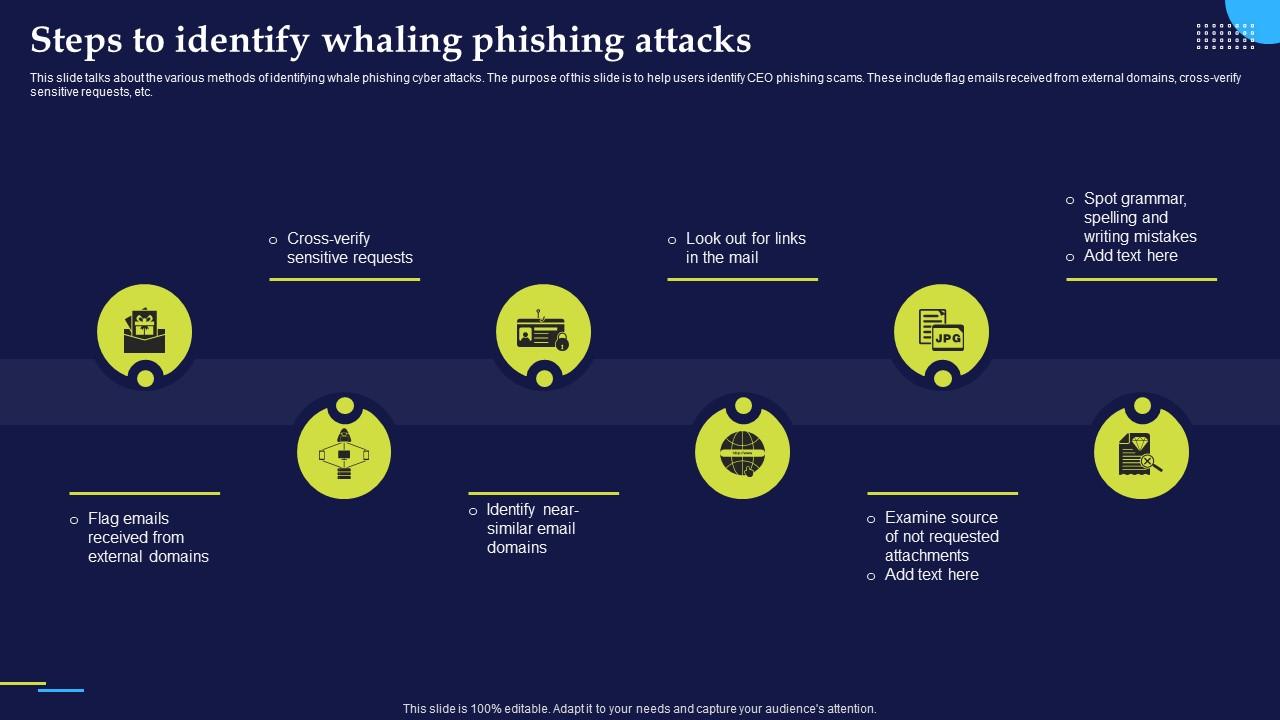 Phishing Attacks And Strategies To Mitigate Them V2 Steps To Identify Phishing Attacks And Strategies To Mitigate Them V2 Steps To Identify
Phishing Attacks And Strategies To Mitigate Them V2 Steps To Identify Phishing Attacks And Strategies To Mitigate Them V2 Steps To Identify
 Phishing Attacks And Strategies To Mitigate Them V2 Vishing Cyber Scams Phishing Attacks And Strategies To Mitigate Them V2 Vishing Cyber Scams
Phishing Attacks And Strategies To Mitigate Them V2 Vishing Cyber Scams Phishing Attacks And Strategies To Mitigate Them V2 Vishing Cyber Scams
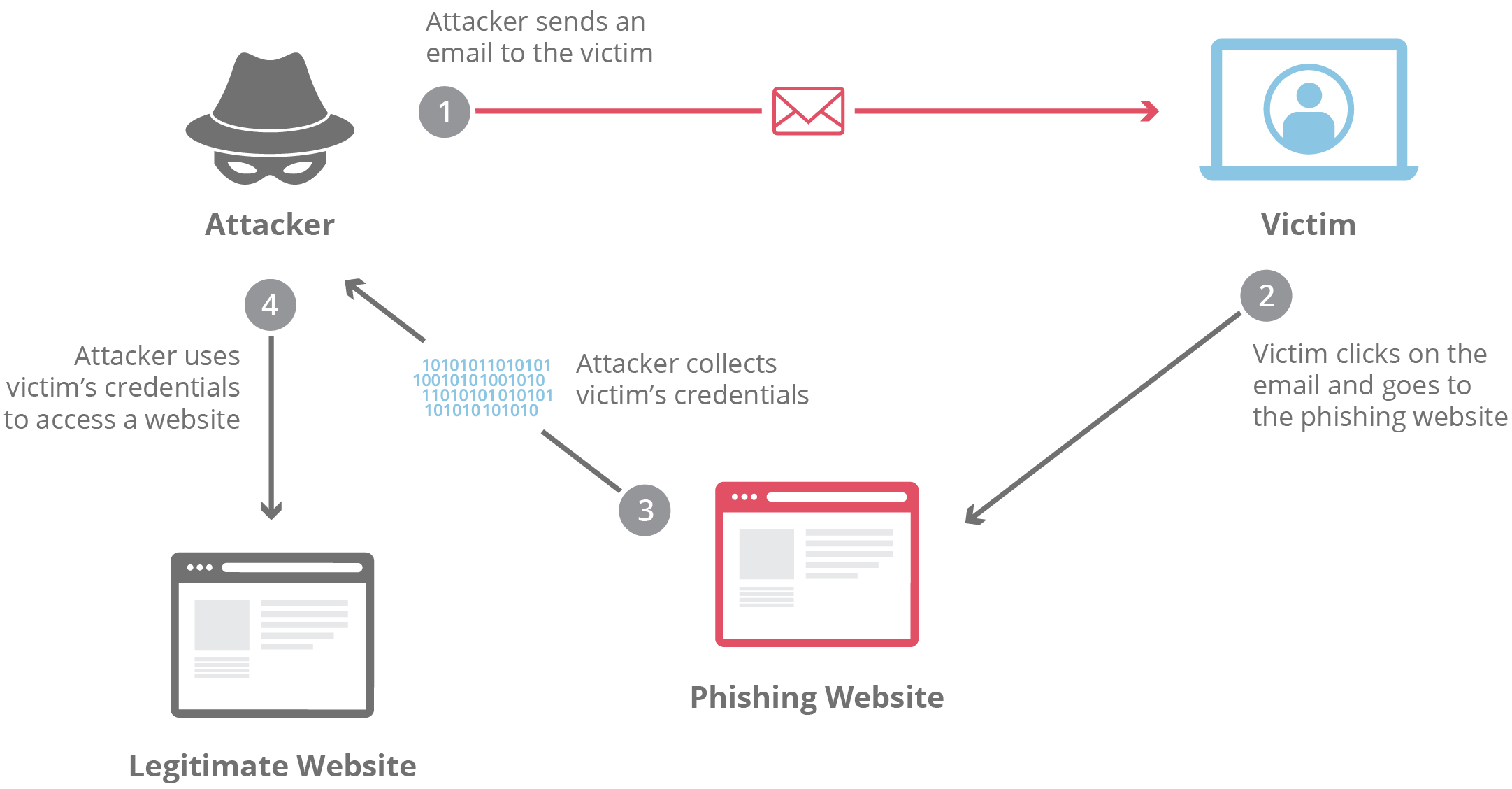 What is a phishing attack? | Cloudflare What is a phishing attack? | Cloudflare
What is a phishing attack? | Cloudflare What is a phishing attack? | Cloudflare
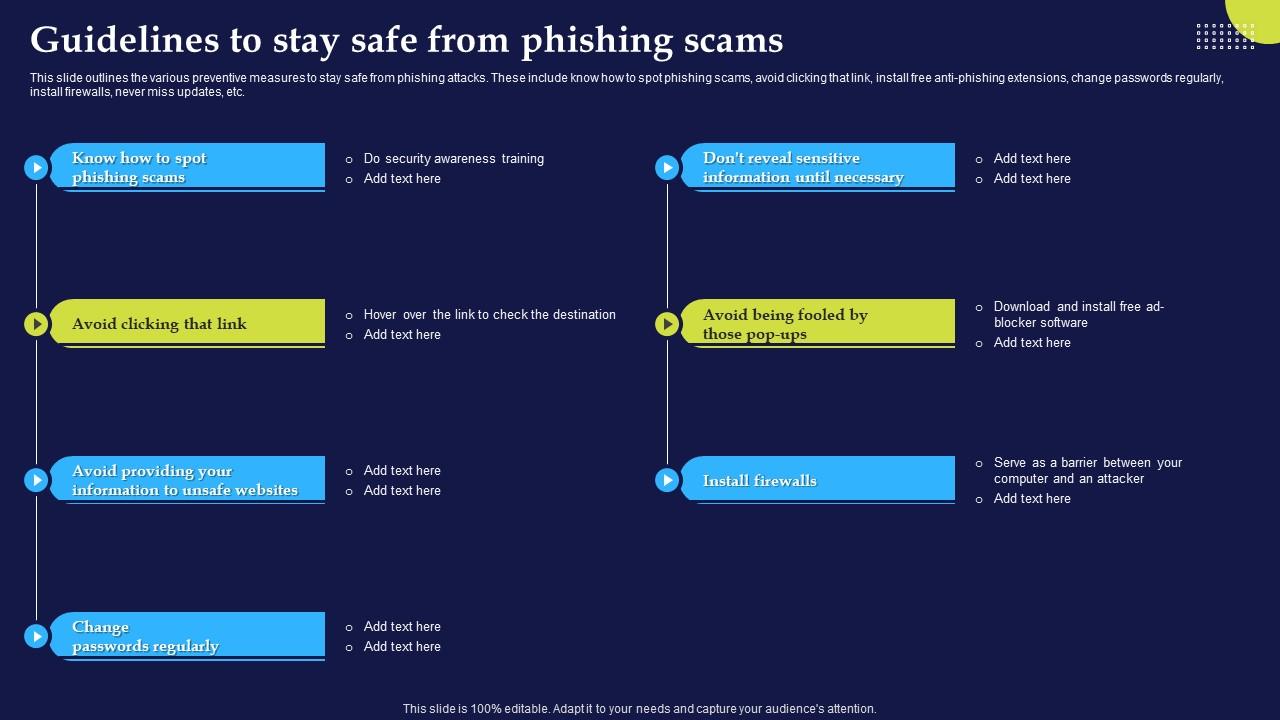 Phishing Attacks And Strategies To Mitigate Them V2 Guidelines To Stay Phishing Attacks And Strategies To Mitigate Them V2 Guidelines To Stay
Phishing Attacks And Strategies To Mitigate Them V2 Guidelines To Stay Phishing Attacks And Strategies To Mitigate Them V2 Guidelines To Stay
 Phishing Attacks And Strategies To Mitigate Them V2 Primary Techniques Phishing Attacks And Strategies To Mitigate Them V2 Primary Techniques
Phishing Attacks And Strategies To Mitigate Them V2 Primary Techniques Phishing Attacks And Strategies To Mitigate Them V2 Primary Techniques
 Phishing Attacks And Strategies To Mitigate Them Powerpoint Phishing Attacks And Strategies To Mitigate Them Powerpoint
Phishing Attacks And Strategies To Mitigate Them Powerpoint Phishing Attacks And Strategies To Mitigate Them Powerpoint
 Phishing Attacks And Strategies To Mitigate Them Powerpoint Phishing Attacks And Strategies To Mitigate Them Powerpoint
Phishing Attacks And Strategies To Mitigate Them Powerpoint Phishing Attacks And Strategies To Mitigate Them Powerpoint
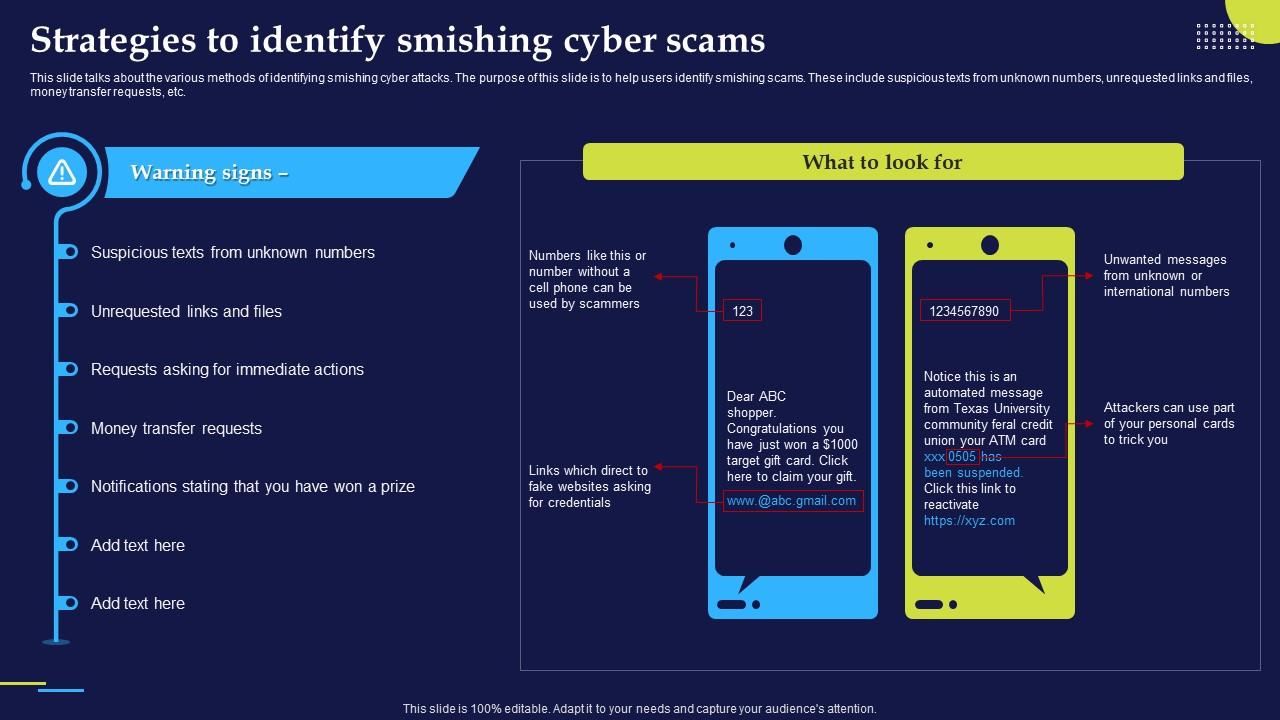 Phishing Attacks And Strategies To Mitigate Them V2 Strategies To Phishing Attacks And Strategies To Mitigate Them V2 Strategies To
Phishing Attacks And Strategies To Mitigate Them V2 Strategies To Phishing Attacks And Strategies To Mitigate Them V2 Strategies To
 Agenda For Phishing Attacks And Strategies To Mitigate Them V2 Ppt Agenda For Phishing Attacks And Strategies To Mitigate Them V2 Ppt
Agenda For Phishing Attacks And Strategies To Mitigate Them V2 Ppt Agenda For Phishing Attacks And Strategies To Mitigate Them V2 Ppt
 Phishing Attacks And Strategies To Mitigate Them V2 About Smishing Phishing Attacks And Strategies To Mitigate Them V2 About Smishing
Phishing Attacks And Strategies To Mitigate Them V2 About Smishing Phishing Attacks And Strategies To Mitigate Them V2 About Smishing
 Phishing Attacks And Strategies To Mitigate Them Powerpoint Phishing Attacks And Strategies To Mitigate Them Powerpoint
Phishing Attacks And Strategies To Mitigate Them Powerpoint Phishing Attacks And Strategies To Mitigate Them Powerpoint
 K106 Warning Signs To Recognize Phishing Email Phishing Attacks And K106 Warning Signs To Recognize Phishing Email Phishing Attacks And
K106 Warning Signs To Recognize Phishing Email Phishing Attacks And K106 Warning Signs To Recognize Phishing Email Phishing Attacks And
 Phishing Attacks And Strategies To Mitigate Them Powerpoint Phishing Attacks And Strategies To Mitigate Them Powerpoint
Phishing Attacks And Strategies To Mitigate Them Powerpoint Phishing Attacks And Strategies To Mitigate Them Powerpoint
 Phishing Attacks And Strategies To Mitigate Them Powerpoint Phishing Attacks And Strategies To Mitigate Them Powerpoint
Phishing Attacks And Strategies To Mitigate Them Powerpoint Phishing Attacks And Strategies To Mitigate Them Powerpoint
 Phishing Attacks And Strategies To Mitigate Them V2 About Search Engine Phishing Attacks And Strategies To Mitigate Them V2 About Search Engine
Phishing Attacks And Strategies To Mitigate Them V2 About Search Engine Phishing Attacks And Strategies To Mitigate Them V2 About Search Engine
 Phishing Attacks And Strategies To Mitigate Them V2 Powerpoint Phishing Attacks And Strategies To Mitigate Them V2 Powerpoint
Phishing Attacks And Strategies To Mitigate Them V2 Powerpoint Phishing Attacks And Strategies To Mitigate Them V2 Powerpoint
 Phishing Attacks And Strategies To Mitigate Them V2 Steps To Take After Phishing Attacks And Strategies To Mitigate Them V2 Steps To Take After
Phishing Attacks And Strategies To Mitigate Them V2 Steps To Take After Phishing Attacks And Strategies To Mitigate Them V2 Steps To Take After
 Phishing Attacks And Strategies To Mitigate Them V2 Real World Examples Phishing Attacks And Strategies To Mitigate Them V2 Real World Examples
Phishing Attacks And Strategies To Mitigate Them V2 Real World Examples Phishing Attacks And Strategies To Mitigate Them V2 Real World Examples
 K103 Identification And Prevention Of Spear Phishing Attacks And K103 Identification And Prevention Of Spear Phishing Attacks And
K103 Identification And Prevention Of Spear Phishing Attacks And K103 Identification And Prevention Of Spear Phishing Attacks And
 Phishing Attacks And Strategies To Mitigate Them V2 Powerpoint Phishing Attacks And Strategies To Mitigate Them V2 Powerpoint
Phishing Attacks And Strategies To Mitigate Them V2 Powerpoint Phishing Attacks And Strategies To Mitigate Them V2 Powerpoint
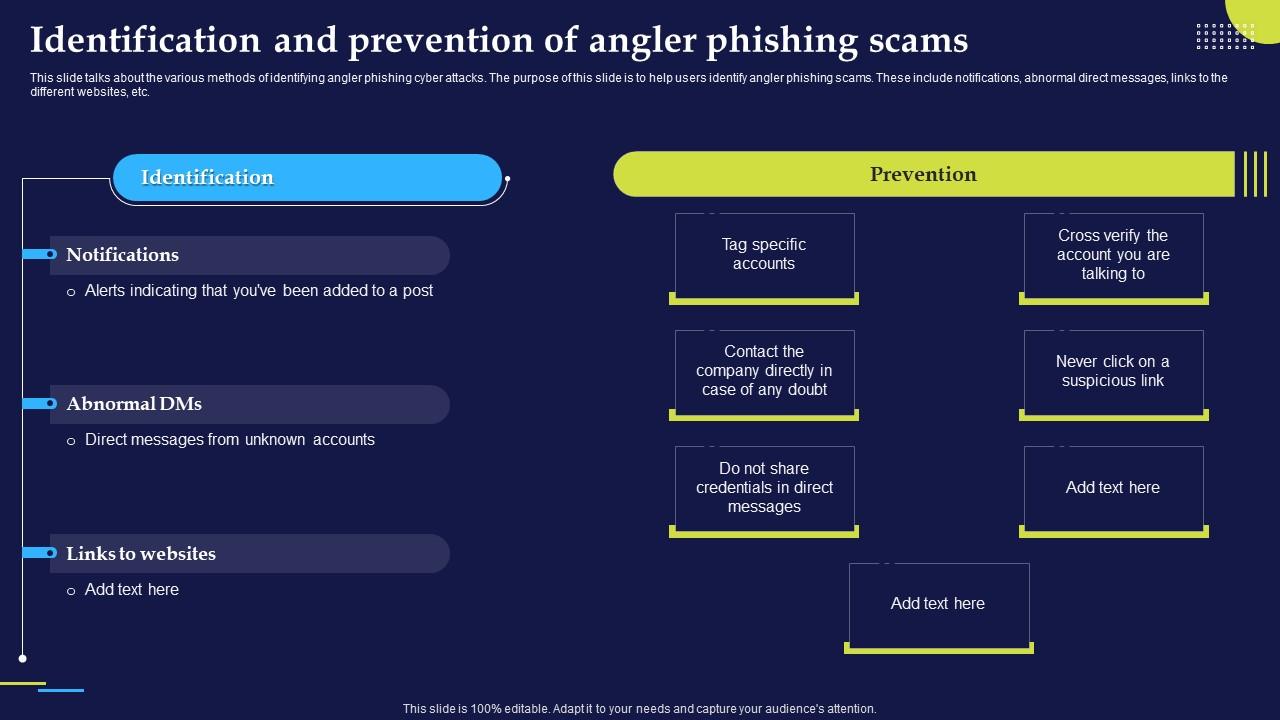 Phishing Attacks And Strategies To Mitigate Them V2 Identification And Phishing Attacks And Strategies To Mitigate Them V2 Identification And
Phishing Attacks And Strategies To Mitigate Them V2 Identification And Phishing Attacks And Strategies To Mitigate Them V2 Identification And

